Digital Age – How to approach Cyber Security
Andreas von Grebmer | CIS Switzerland.
A risk-based approach to information security considering the human factor
In June 2017 a first chapter of the book was released on www.security-finder.ch prior to the finalization of the new release. The chapter 1.1 Information Security Stumbling Blocks outlined that the root cause of most security risks, threats and incidents are humans.
For example, if a security incident arises because of “Misconfiguration, initial configuration not changed”, the human factor caused this “Technology not understood, laziness, time pressure”. If your answer to this is more security technology, you end up in the vicious circle of Information Security. A thoughtful root cause analysis could reveal that technology knowledge was missing, testing time in the deployment project was cut, existing processes and hardening guidelines were not followed etc.. Hence human and enterprise cultural flaws led to the issue, which you will never fix with more technology.
Adding Security Technology is not bad, but before doing that, you could gain much more quick wins with much less budget if you address human and enterprise cultural flaws first. And this can be as easy (or hard) as senior management really taken care of Cyber Security.
Information is the live blood of an enterprise. Any threats to information should have full attention of the leadership team.
Most companies today have a traditional approach to Information-/Cybersecurity with typical shortcomings, explained in chapter
1.3 Traditional Information Security
What do I mean by traditional information security? I met dozens of CISOs and information security officers and all of them described, more or less, the same set-up and the same problems that arise from these set-ups. If your organizational set-up differs and is more successful, lucky you.
Traditional information security is driven by:
- management identified need to follow regulatory requirements.
- control framework enforced by a compliance organization, e.g. Security Officer.
- Awareness training to prove compliance.
- Hype topics mainly created externally, e.g. cyber security.
If you remove the pressure, the fear, information security awareness will immediately drop.
Or did ever somebody come to you asking for an extra awareness training, without you approaching them?
This approach does not leverage the existing information security related wiring nor does it improve or enhance the wiring. People only follow your awareness training, because there are consequences if they don’t do it. This is the same level as the security instruction in the airplane before take off.
This leads to the conclusion that the approach must be changed going forward.
There is also a chapter for the once that see the need for a change:
1.1 Future Information Security
How should or could it be? Always assuming that you see and acknowledge the dilemma of the traditional information security and you want to transform your organization.
Since there is no ideal world, future information security can only be a better approach, more adapted to the current society set-up. It will not be a perfect approach.
If your intent is to transform, you first need to analyze the current situation exactly. This analysis must be ruthless and brutally honest.
Indicators of how your new information security set-up should be:
- Information security is a mindset, management acts as role model.
- Information security is evaluated for everything.
- Information security is implemented for information and information processing assets based on defined criticality levels.
- Criticality of information and the information processing assets are re-evaluated on a defined schedule.
- Business/owners raise triggers for re-evaluation, in case of major changes, on their own.
- Reaction and recovery when the hit is fast (resilience).
- Individuals have no fear to speak up and to report own mistakes.
Learn from the immune system when you set up your information security program.
A key thought for the possible future set-up is to reset the organization regarding accountability for information security. Traditionally the person responsible for security is held accountable for defining, implementing and controlling the measures needed for information security.
1. Give the accountability for information security back where it belongs.
2. Your information security set-up needs to affect everyone and vice versa.
This will lower the resources in the security department.
You are responsible for your own health, not your doctor. The same is true for information security. In most countries, even by law, the highest management has the overall accountability, this includes information security as well as governance, risk and compliance. Where most companies’ senior managers care about governance, risk and compliance for obvious reasons, especially in regulated industries like banking and healthcare, information security is not tangible, not sexy and often not understood. So it is shifted away from business relevant functions and often it ends up in IT, a function that is seen to provide commodity services and is therefore more likely to be outsourced.
If you like the idea and think it makes sense, you specially need to take care of the transition as described in the next chapter. Depending on the current set-up, such a change can be dramatic and needs to be well planned and equally importantly, communication must be unambiguous. Change management is key. Find out if you have an organizational change management specialist who could support you in the process.
Have a look at the app store for “KPN CISO KSP application”. This is how information security can be done in an innovative way. Do not focus so much on the detailed functionality, because for your organization, it will need to be different. The intent, the transparency for all users is what counts.
The idea is to build a solid “The house of information risk management”.
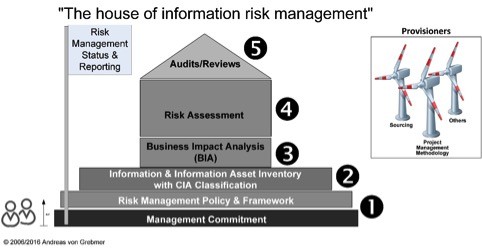

The two symbols on the lower left corner show that you need time and a supporting organization to build your house of information risk management.
The house is only effective if it is built bottom up layer by layer. If you skip layer, the sustainability is not given.
Diagram 42: Information assurance committee
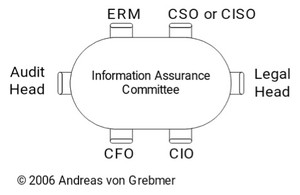

The information assurance committee should meet at least twice a year and take necessary decisions to set a clear strategy and bundle or assign resources for information assurance.
Quelle: Text und Grafiken «Digital Age – How to approach Cyber Security»
Erhältlich auf Amazon
Auch als eBook erhältlich.
Verlag: Books on Demand
Autor: Andreas von Grebmer
Erscheinungsjahr: 2017
ISBN: 978-3744871464